
Protection
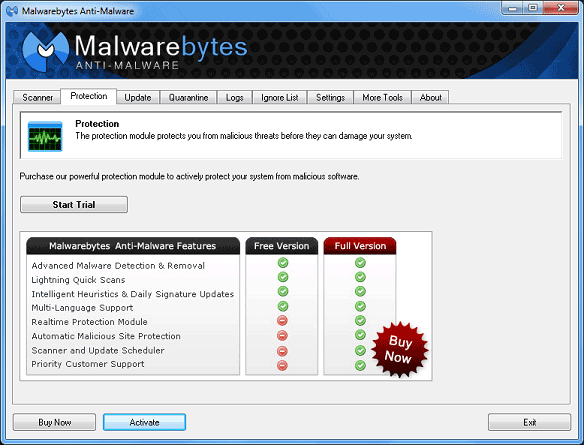
In the unregistered version of Malwarebytes Anti-Malware, the
protection tab shows a comparison of the two versions, highlighting the added
features available in the PRO Version. Clicking on the comparison image
takes the user to the Malwarebytes Anti-Malware online store.
In the registered version of Malwarebytes Anti-Malware, the
protection tab displays various options now available to protect the system
from malicious threats, utilizing the advanced protection module along with the
scheduler.
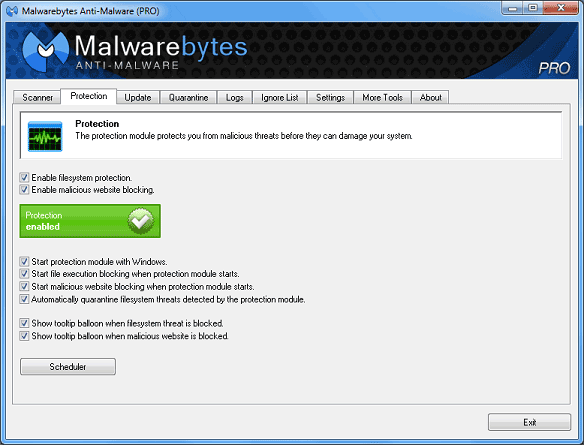
- Enable filesystem protection: Malicious file execution blocking is
enabled. If the tray icon for the protection module is not already running,
it will start and will enable both protection components if they are both
set to start when the protection module starts. If the tray icon is already
running, it will simply enable or disable Filesystem Protection.
- Enable malicious website blocking: Malicious website
blocking is enabled. If the tray icon for the protection module is not
already running, it will start and will enable both protection components
if they are both set to start when the protection module starts. If the
tray icon is already running, it will simply enable or disable Website
Blocking
- Start protection module with Windows: This option will start the
Protection Module during system startup and place a tray icon in the system
tray.
- Start file execution blocking when protection module starts: This
option detects and blocks malicious processes and prompts the user to take
action upon detection.
- Start malicious website blocking when protection module starts:
This option blocks access to known malicious websites.
- Automatically quarantine filesystem threats detected by the
protection module: This option will quarantine infected files
detected by the protection module automatically. When this setting is
disabled, the user will be prompted to take an action. The three available
actions are 'Quarantine' which will block the threat from running and
quarantine the file, 'Allow Temporarily' which will allow the threat to run
one time but will block the threat if it attempts to run at a later time,
and 'Allow Always' which will add the threat to the Ignore List.

- Show tooltip balloon when filesystem threat is blocked:
This option will generate a tray icon notification whenever a filesystem
threat is quarantined. The 'Automatically quarantine filesystem threats
detected by the protection module' setting must be enabled for this option
to function.
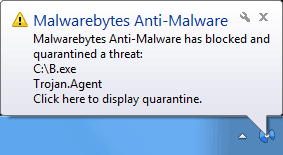
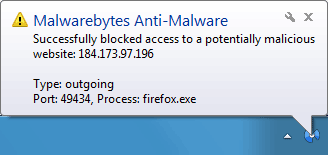
- Show tooltip balloon when malicious website is blocked: This
option will generate a tray icon notification whenever a malicious IP
address is blocked. Details such as the application name, the connection
type as well as the port number are shown on Windows Vista and higher
operating systems.
- Scheduler: Allows the user to schedule scans and updates to fit
individual needs. An optional predefined update is included during
activation. See the Scheduler section for details.
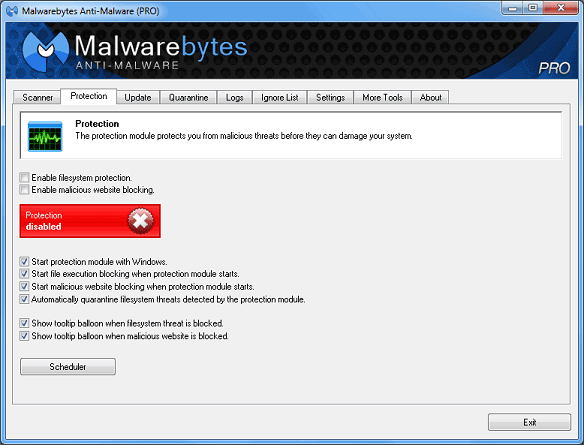
The protection tab also displays the current status of the protection
module. If the tray, which controls and enables all components of the
protection module is disabled, the following is shown.
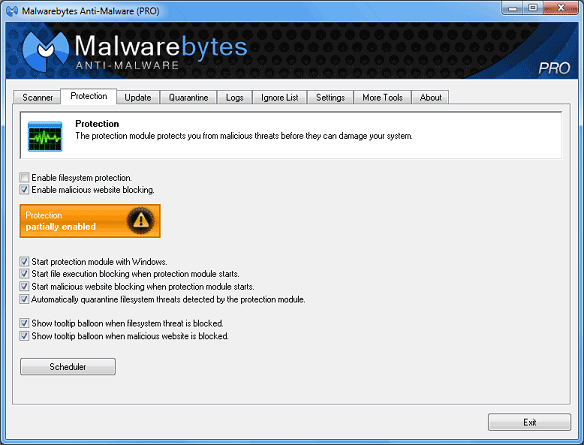
If only one of the components of the protection module is disabled, the
following is shown.
If both components of the protection module are enabled, the following is
shown.












